Configuring Local Database for Management User Authentication
You can configure the device to use the Local Users table (local database) to authenticate management users based on username-password combination. You can configure the device to use the Local Users table (see Configuring Management User Accounts) upon the following scenarios:
|
■
|
LDAP or RADIUS server is not configured (or broken connection) or always use the Local Users table and only if the user is not found, to use the server. |
|
■
|
Connection with the LDAP or RADIUS server fails due to a timeout. In such a scenario, the device can deny access or verify the user's credentials (username-password) locally in the Local Users table. |
If user authentication using the Local Users table succeeds, the device grants management access to the user; otherwise access is denied. The access level assigned to the user is also determined by the Local Users table.
|
●
|
This feature is applicable to LDAP and RADIUS. |
|
●
|
This feature is applicable only to user management authentication. |
|
➢
|
To use the Local Users table for authenticating management users: |
|
1.
|
Open the Authentication Server page (Setup menu > Administration tab > Web & CLI folder > Authentication Server). |
|
2.
|
Under the General group, do the following: |
|
a.
|
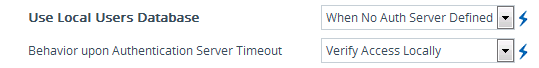
Configure when the Local Users table must be used to authenticate login users. From the 'Use Local Users Database' drop-down list, select one of the following: |
|
◆
|
When No Auth Server Defined (default): When no LDAP/RADIUS server is configured or if a server is configured but connectivity with the server is down (if the server is up, the device authenticates the user with the server). |
|
◆
|
Always: First attempts to authenticate the user using the Local Users table, but if not found, it authenticates the user with the LDAP/RADIUS server. |
|
a.
|
Configure whether the Local Users table must be used to authenticate login users upon connection timeout with the server. From the 'Behavior upon Authentication Server Timeout' drop-down list, select one of the following: |
|
◆
|
Deny Access: User is denied access to the management platform. |
|
◆
|
Verify Access Locally (default): The device verifies the user's credentials in the Local Users table. |
|
3.
|
Click Apply, and then reset the device with a save-to-flash for your settings to take effect. |
